
New Insikt Group research discusses the frequent abuse of GitHub’s services by cybercriminals and advanced persistent threats (APTs) for various malicious infrastructure schemes. These include payload delivery, dead drop resolving (DDR), full command-and-control (C2), and exfiltration. GitHub’s popularity among threat actors lies in its ability to allow them to blend in with legitimate network traffic, making detection and attribution challenging for defenders.
The “living-off-trusted-sites” (LOTS) approach is highlighted as a growing trend among APTs, with less-sophisticated groups expected to follow suit. The text suggests a short-term strategy for defenders to flag or block specific GitHub services known for malicious use. In the long term, organizations are encouraged to invest resources in understanding how GitHub and other code repositories are abused, leading to the development of more sophisticated detection mechanisms.
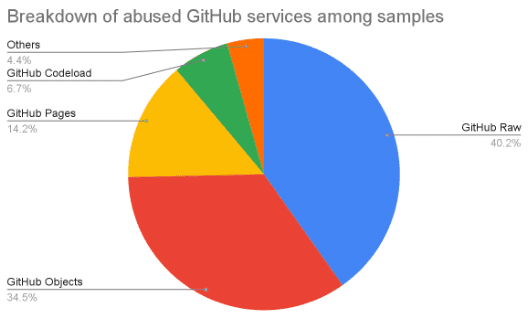
Breakdown of abused GitHub services among samples from March to November 2023 (Source: Recorded Future)
As attacks are anticipated to increase, the text emphasizes that legitimate internet services (LIS) will pose a new third-party risk vector for customers. Mitigation strategies are expected to require advanced detection methods, comprehensive visibility, and diverse detection angles. The responsibility for combating abuse may shift to LIS through structural changes and product innovations, leveraging their unique visibility into user and usage data.
The primary infrastructure schemes for GitHub abuse are detailed, with payload delivery being the most prevalent due to its ease of implementation. GitHub is also commonly used for DDR, full C2 (linked to APT activity), and exfiltration, although the latter is less common. GitHub services are abused for various other malicious purposes, including hosting phishing operations and serving as an infection vector through repository poisoning techniques.
The research acknowledges that there is no universal solution for GitHub abuse detection, emphasizing the need for a mix of detection strategies tailored to specific environments, organizational structures, and risk tolerances. Overall, defenders are urged to allocate more resources to combat GitHub abuse, and LIS is expected to play a more significant role in addressing the issue through policy changes and technical innovations.
To read the entire analysis, click here to download the report as a PDF.
link

